Security
Information Systems Security – How do we protect our systems: people, processes, Data, HW & SW?
Often perceived as a trade off Security vs. Freedom
- Freedom to choose passwords
- Frequency of changing passwords
- Follow strict rules for Passwords (Stronger)
- Dual Authentication (Stronger Still)
Really a trade off Risk vs. Cost
Defining Risk
Committee on National Security Systems
A combination of: the likelihood that a threat will occur, the likelihood that a threat occurrence will result in an adverse impact, the severity of the resulting impact
National Institute of Standards and Technology (NIST)
Risk is a function of the likelihood of a given threat-source’s exercising a particular potential vulnerability, and the resulting impact of that adverse event on the organization.
Wikipedia
IT risk: the potential that a given threat will exploit vulnerabilities of an asset or group of assets and thereby cause harm to the organization. It is measured in terms of a combination of the probability of occurrence of an event and its consequence.
All have common key elements:
- Asset (something of value)
- Vulnerability that can be exploited (includes data center, processes, people, as well asSW)
- Exploit of a vulnerability (could be caused by a person, organization, or event)
Can Risk be measured?
- There are four fundamental forces involved in risk management, which also apply to cybersecurity. They are assets, impact, threats, and likelihood. You have internal knowledge of and a fair amount of control over assets, which are tangible and intangible things that have value. You also have some control over impact, which refers to loss of, or damage to, an asset. However, threats that represent adversaries and their methods of attack are external to your control. Likelihood is the wild card here. Likelihood is the probability that if and when a threat will materialize, succeed, and do damage. While never fully under your control, likelihoods can be shaped and influenced to manage the risk.
- With Hackers (vs Natural disasters), another way to look at this might be to define Threat as the likelihood that a vulnerability will be exploited. Risk then would be the potential for loss or damage when a vulnerability is exploited.
- Threat Analysis Group (TAG) offers a simple formula
- Risk = Asset + Threat + Vulnerability
- Mathematically, the forces could be represented in a formula such as:
- Risk = p(Asset,Threat) times d(Asset,Threat)
- where p() is the likelihood that a Threat will materialize/succeed against an Asset, and d() is the likelihood of various levels of damage that may occur.
For Example:
- You maintain employee social security numbers and DOB in a payroll system so that you can pay them. What are the risk factors here? Who is at risk? How do you mitigate the risk?
- You have a retail POS system with credit card data for your customers. What are the risk factors here? Who is at risk? How do you mitigate the risk?
- You are a large global law firm specializing in mergers and acquisitions; What are the risk factors here related to M&A? Who is at risk? How do you mitigate the risk?
- You have daily weekly and monthly backups running and you keep backups for specified time periods (e.g. financials for 7 years following a GFS system.)
- Your data center is open to anyone in the organization and has an old roof that occasionally leaks.
Safeguards: How to mitigate risk?
If we are concerned about threats that could interrupt our business or seek to obtain or alter data or other IT assets illegally, without permission, and without the owner’s knowledge.
We can then look at a Safeguard as some measure that individuals or organizations take to block the threat from impacting the asset. In the diagram below it is represented by a brick wall, however this is not referencing only firewalls, which are one type of safeguard (see chart below).
Target = the asset that is desired by the threat.
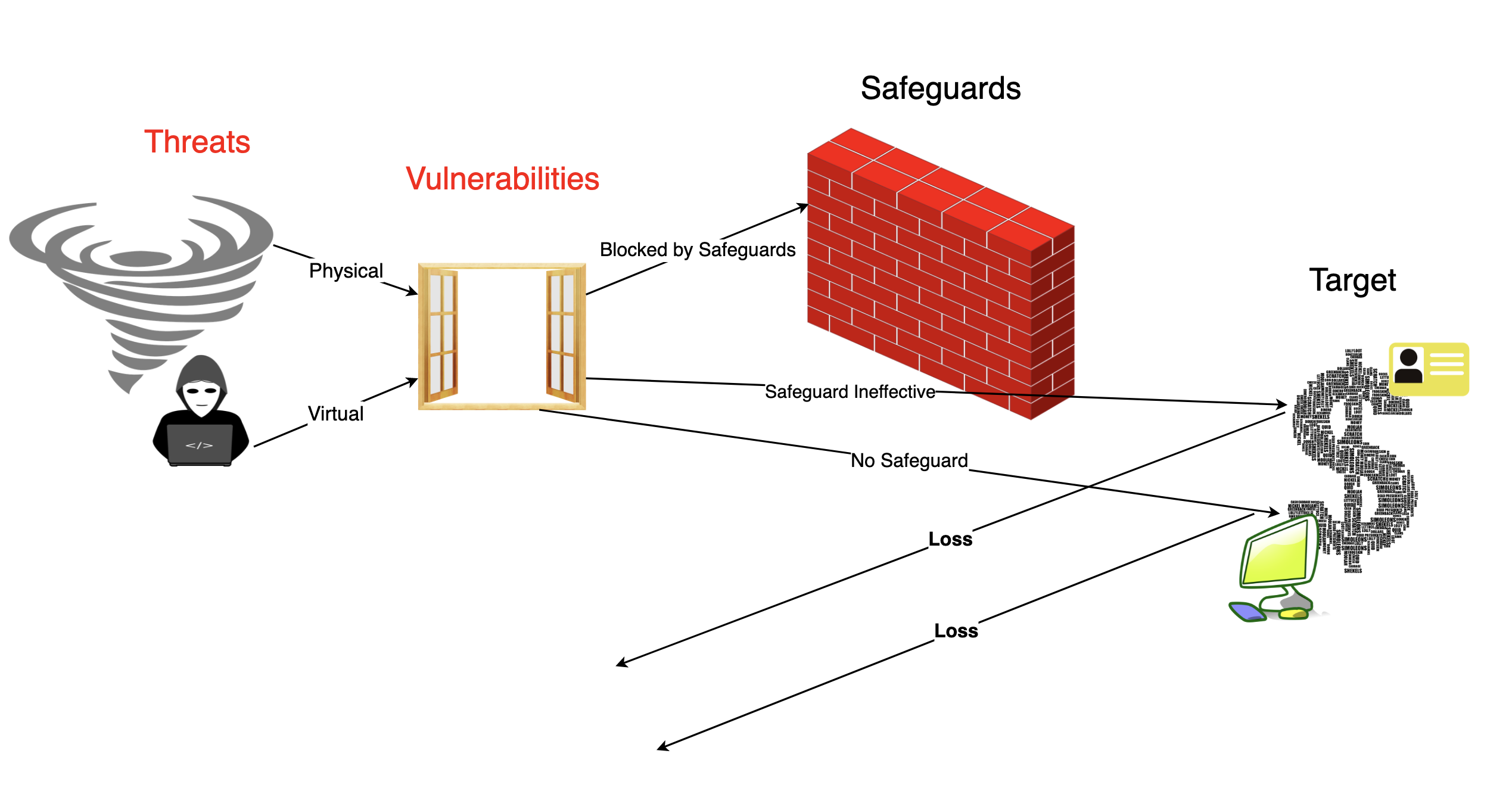
Threats can be stopped, or if not stopped, the costs of loss can be reduced by creating appropriate safeguards. Safeguards are, however, expensive to create and maintain – loss of freedom is also a cost. Safeguards can reduce work efficiency by making common tasks more difficult, adding additional labor expense. The goal of information security is to find an appropriate trade-off between the risk of loss and the cost of implementing safeguards.
Examples – Threat -Vulnerability – Safeguard:
| Threat/Target | Vulnerability | Safeguard | Outcome | Effectiveness of Safeguard |
|---|---|---|---|---|
| Hacker wants to steal your bank login credentials | Hacker creates a phishing site nearly identical to your online banking site. | Only access the site using “https” at the beginning of the URL. | No loss | Effective safeguard |
| Hacker wants to steal your bank login credentials | Hacker creates a phishing site nearly identical to your online banking site. | None | You access the phishing site and hacker gains your credentials. | Ineffective safeguard |
| Employee posts sensitive data to public Google group | Public access to not-secure group | Password Procedures, Employee Training | Loss of sensitive data | Ineffective safeguard |
Row 1 – Safeguard effective no loss
Row 2 – Safeguard/No Safeguard – Asset – Login Credentials
Row 3 – Human error posting to wrong group Asset – sensitive data Passwords and procedures ineffective.
Table of types of threats to consider
| Type of loss | Human Error
(i.e. accidentally post to wrong group or delete records) |
Computer Crime
(Employees, former employees, hackers) |
Natural Disasters
(Fire, flood, hurricane, earthquake, power, comms, etc.) |
|---|---|---|---|
| Unauthorized Data Disclosure | From procedural mistakes | From:
|
Due to disclosure during recovery after disaster event |
| Incorrect Data Modification | From:
|
From hacking | Due to incorrect data recovery after disaster event |
| Faulty Service | From:
|
From Usurpation | Service improperly restored after disaster event |
| Denial of Service | From accidents | From DoS attacks | Service interruptions during disaster event |
| Loss of infrastructure | From accidents | From Theft, or Terrorist activity | Due to property loss from disaster event
|
Examples :
- Unauthorized Data Disclosure – obtains data that is supposed to be protected.
- Pretexting – pretend to be someone else, phone call from cc company, or Msft.
- Phishing – ask for data.
- Spoofing – pretend to be a specific person. IP spoofing – pretend to be another site.
- Sniffing – intercept
- Incorrect Data Modification
- Increase a discount, grant more credit, increase a salary, change a grade
- Faulty Service
- Incorrect system operation.
- Incorrect Data Modification
- Send wrong goods to a customer
- Send unordered goods to a customer
- Can be a programming or procedural error
- Usurpation – replace a program with a new version (their own.)
- Incorrect system operation.
- Denial of Service – Service Unavailable
- Human Error – shut down server
- Consumer too many resources
- DDOS attack Distributed Denial of Service
- Loss of Infrastructure
- Human Error/Accident – Fiber Cut
- Disgruntled Employee
- Natural disaster – largest risk
- APT – Advance Persistent Threat – Long running attack siphon data without being discovered
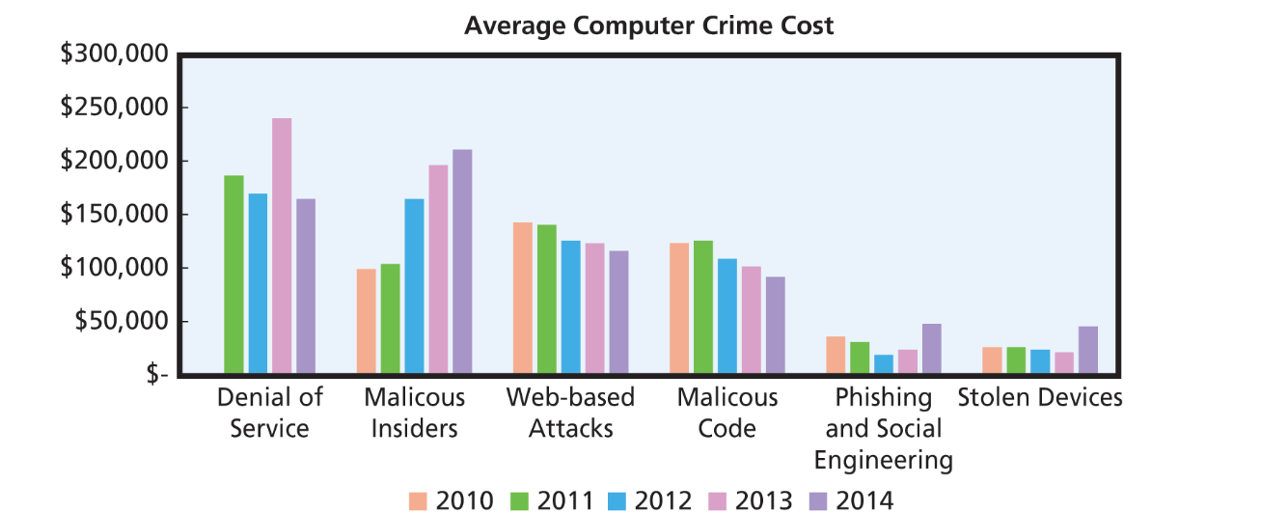
Historical view of type of attacks and costs (frequency and size of loss.)
| Type of Attack | 2010 | 2011 | 2012 | 2013 | 2014 |
|---|---|---|---|---|---|
| Denial of Service | N/A | $187,506 (17%) | $172,238 (20%) | $242,913 (21%) | $166,545 (18%) |
| Malicious Insiders | $100,300 (11%) | $105,253 (9%) | $166,251 (8%) | $198,769 (8%) | $213,542 (8%) |
| Web-based attacks | $143,209 (15%) | $141,647 (12%) | $125,794 (13%) | $125,101 (12%) | $116,424 (14%) |
| Malicious Code | $142,083 (26%) | $126,787 (23%) | $109,533 (26%) | $102,216 (21%) | $19,500 (23%) |
| Phishing and Social Engineering | $35,514 (12%) | $30,397 (9%) | $18,040 (7%) | $21,094 (11%) | $45,959 (13%) |
| Stolen Devices | $25,663 (17%) | $24,968 (13%) | $23,541 (12%) | $20,070 (9%) | $43,565 (10%) |
Most of increase appears to be malicious insiders – includes current & former employees, temps, contractors and business partners.
Ponemon surveyed losses by type of asset as well. It found that the business disruption was single most expensive consequence of computer crime. (How has this been impacted by the accelerated transaction pace and revenue cycles we have seen over the last two decades?)
Source: Based on Ponemon Institute, 2014 Cost of Cyber Crime study: United States October 2014, P.12.
How else can we mitigate risk?
- Practices
- Secure Design Principles, Encryption of Data
- Server patching cycle/window
- Strong Password policy: Strong passwords, Change frequently
- Data Policy
- Encrypt (transform clear text into coded, unintelligible text for secure storage or communication.)
- Block downloads
- Account Administration
- Account Management
- Password Management (help desk reset – identify user)
- Identity and Access and assessment at least annually tied to roles/position descriptions
- WISP (Written Information Security Program) Set Policy, Disseminate and enforce
- Responsibility
- Accountability
- Compliance
- Employee and Non Employee
- Roles/Position Descriptions
- Least Privilege you only have access to what you need when you need it.
- Hiring and Screening – Background checks
- Things we implement
- Firewalls Premise, cloud
- IDS – Intrusion Detection System – Looks for patterns, Detects attacks, Identifies repeated attempts
- Antivirus
- SEG (Secure Email Gateway)
- VPN
- Dual Access method (Something you know, Something you have, Something you are)
- Physical Security
- Data Center key cards, man traps? Rely on Cloud vendor?
- Unattended Machines
- Monitor devices Connected to the Network
- Incident Response Plan What will you do when something happens
- Thresholds for severity
- How communicate
- What to Communicate
- When to Communicate
- When to involve Law Enforcement?
Firewall:
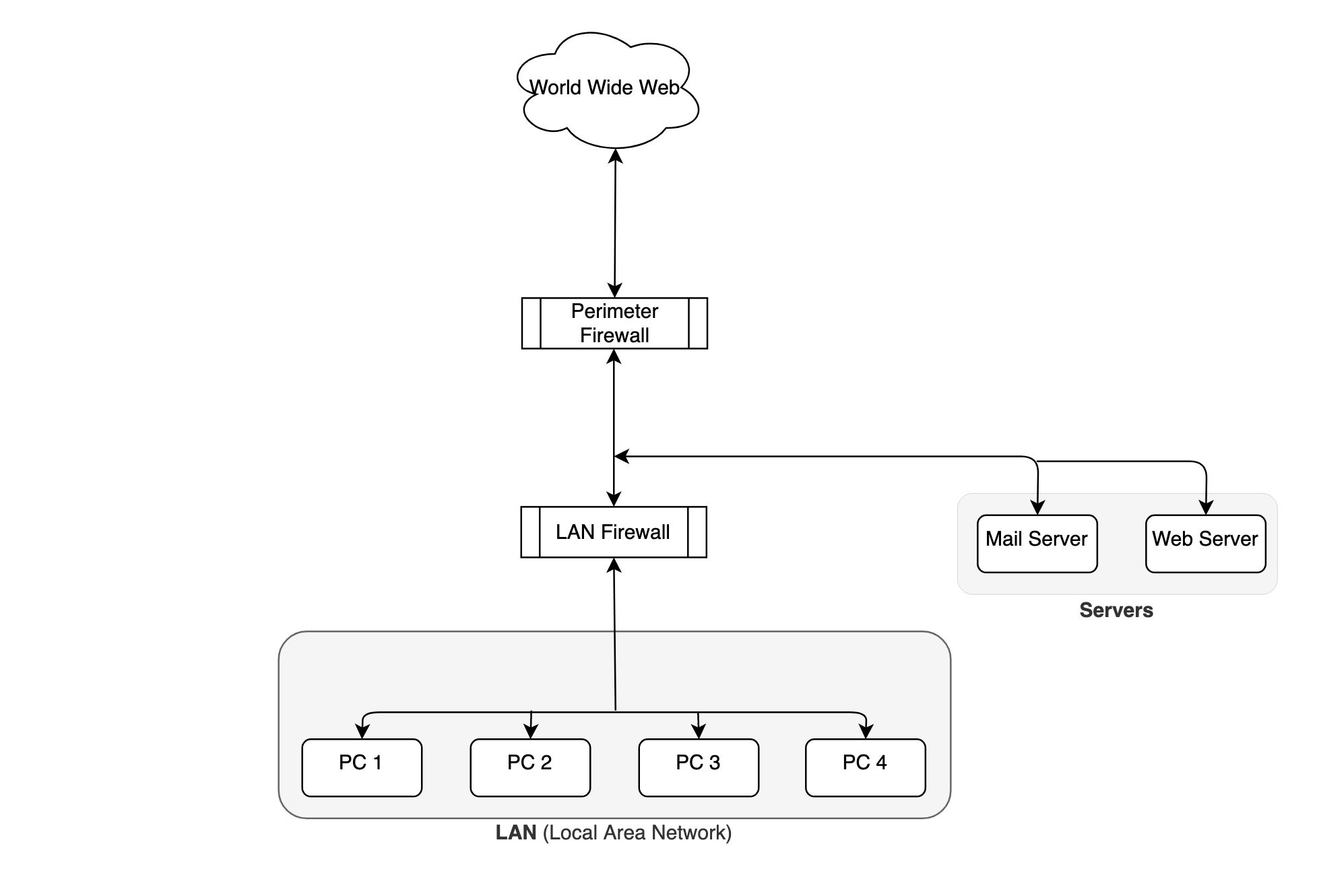
- Firewall – a device that prevents unauthorized network access. Can be a special-purpose computer, or it can be a program on a general-purpose computer or on a router. In essence, a firewall is simply a filter. It can filter traffic in a variety of ways including where network traffic is coming from, what types of packets are being sent, the contents of the packets, and if the packets are part of an authorized connection.
- Perimeter firewall sits outside the organizational network; it is the first device that Internet traffic encounters. In addition to perimeter firewalls, some organizations employ internal firewalls inside the organizational network. Figure above shows the use of a perimeter firewall that protects all of an organization’s computers and a second internal firewall that protects a LAN.
- Stateful Packet inspection
- Packet Filtering
- NAT
- Firewall in the Cloud?
Secure Design – SQL example
SQL Injection
WikiP Tells us that SQL injection is a code injection technique, used to attack data-driven applications, in which nefarious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker). SQL injection must exploit a security vulnerability in an application’s software, for example, when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. SQL injection is mostly known as an attack vector for websites but can be used to attack any type of SQL database.
Common Type – Incorrectly filtered escape characters
- SQL injection can occur when you ask a user for input, like their username/userid, and instead of a name/id, the user gives you an SQL statement that you will unknowingly run on your database.
- Look at the following example which creates a SELECT statement by adding a variable (txtUserId) to a select string. The variable is fetched from user input (getRequestString):
txtUserId = getRequestString(“UserId”);
txtSQL = “SELECT * FROM Users WHERE UserId = ” + txtUserId;
What if I pass you “105 OR 1=1” as userid
SELECT * FROM Users WHERE UserId = 105 OR 1=1;
Always Valid?
SELECT UserId, Name, Password FROM Users WHERE UserId = 105 or 1=1;
Or what if input is 105; DROP TABLE Suppliers
SELECT * FROM Users WHERE UserId = 105; DROP TABLE Suppliers;
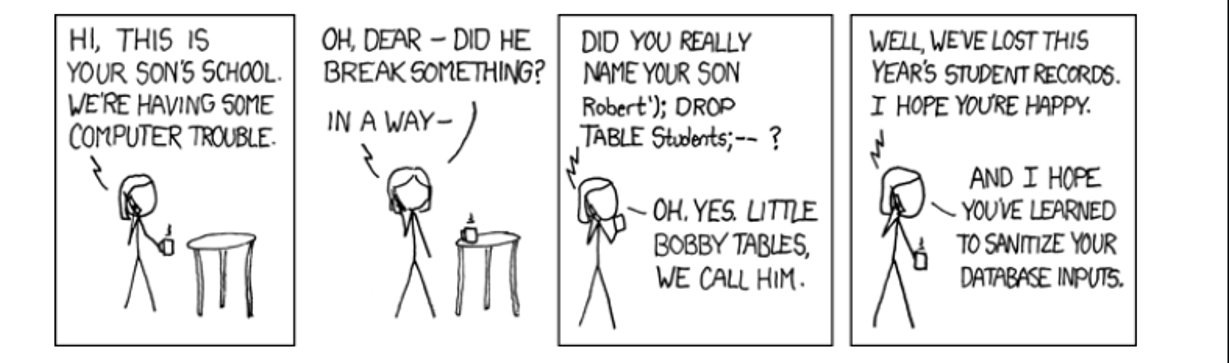
Four panes in a comic. Pane 1 – Hi, this is your sons school. We’re having some computer trouble. Pane 2 – Oh Dear, did he break something? In a way. Pane 3 – Did you really name your son Robert ‘ ) ; Drop table students ;? Oh. yes. Little bobby tables, we call him. Pane 4 – Well we’ve lost this years student records. I hope you’ve learned to sanitize your database inputs.
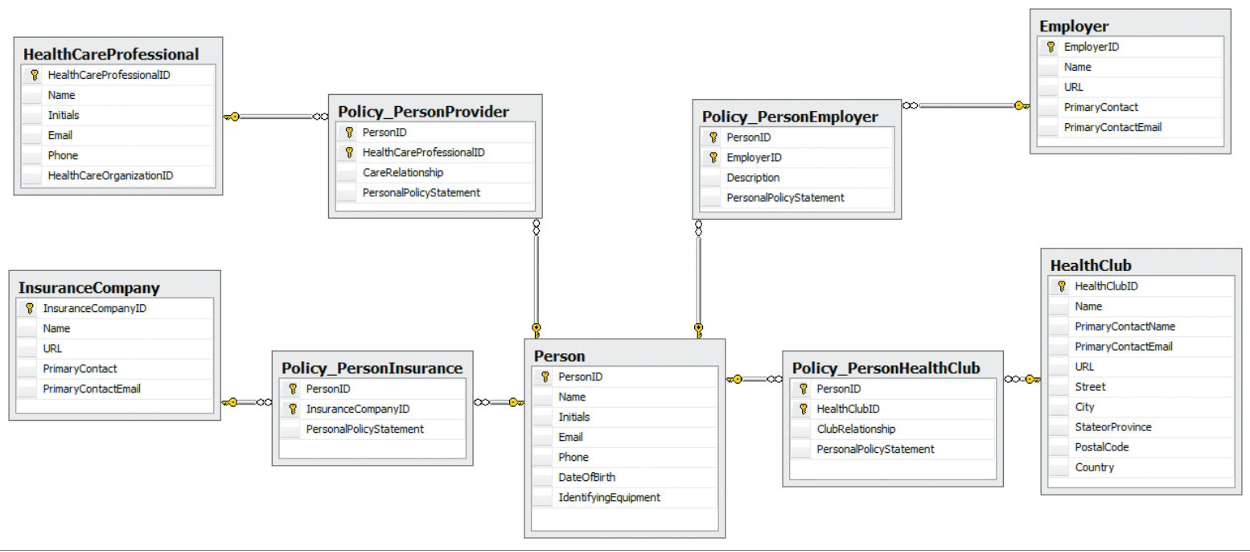
Health Care Application – User managed security
Information owner controls level of access reflected in the policy table (intersection). There are 4 levels the user (owner of the info) can shoose from for each person: None (default), Non Identifying, Summary, and Full Access. The latter two include the persons Identity.
User selects one of the four for each using sharing entity using radio buttons only.