4.1 Analyzing Fraud in the Accounting Workplace
In this chapter, one of the major issues examined is the concept of fraud. Fraud can be defined in many ways, but for the purposes of this course we define it as the act of intentionally deceiving a person or organization or misrepresenting a relationship in order to secure some type of benefit, either financial or nonfinancial. We initially discuss it in a broader sense and then concentrate on the issue of fraud as it relates to the accounting environment and profession.
Workplace fraud is typically detected by anonymous tips or by accident, so many companies use the fraud triangle to help in the analysis of workplace fraud. Donald Cressey, an American criminologist and sociologist, developed the fraud triangle to help explain why law-abiding citizens sometimes commit serious workplace-related crimes. He determined that people who embezzled money from banks were typically otherwise law-abiding citizens who came into a “non-sharable financial problem.” A non-sharable financial problem is when a trusted individual has a financial issue or problem that he or she feels can’t be shared. However, it is felt that the problem can be alleviated by surreptitiously violating the position of trust through some type of illegal response, such as embezzlement or other forms of misappropriation. The guilty party is typically able to rationalize the illegal action. Although they committed serious financial crimes, for many of them, it was their first offense.
The fraud triangle consists of three elements: incentive, opportunity, and rationalization (Figure 4.1). When an employee commits fraud, the elements of the fraud triangle provide assistance in understanding the employee’s methods and rationale. Each of the elements needs to be present for workplace fraud to occur.
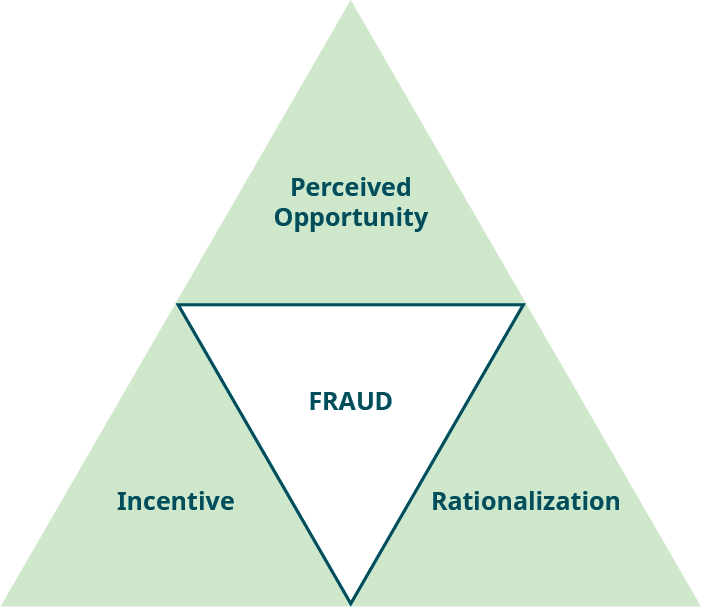
Perceived opportunity is when a potential fraudster thinks that the internal controls are weak or sees a way to override them. This is the area in which an accountant has the greatest ability to mitigate fraud, as the accountant can review and test internal controls to locate weaknesses. After identifying a weak, circumvented, or nonexistent internal control, management, along with the accountant, can implement stronger internal controls.
Rationalization is a way for the potential fraudster to internalize the concept that the fraudulent actions are acceptable. A typical fraudster finds ways to personally justify his or her illegal and unethical behavior. Using rationalization as a tool to locate or combat fraud is difficult, because the outward signs may be difficult to recognize.
Incentive (or pressure) is another element necessary for a person to commit fraud. The different types of pressure are typically found in (1) vices, such as gambling or drug use; (2) financial pressures, such as greed or living beyond their means; (3) work pressure, such as being unhappy with a job; and (4) other pressures, such as the desire to appear successful. Pressure may be more recognizable than rationalization, for instance, when coworkers seem to be living beyond their means or complain that they want to get even with their employer because of low pay or other perceived slights.
Typically, all three elements of the triangle must be in place for an employee to commit fraud, but companies usually focus on the opportunity aspect of mitigating fraud because, they can develop internal controls to manage the risk. The rationalization and pressure to commit fraud are harder to understand and identify. Many organizations may recognize that an employee may be under pressure, but many times the signs of pressure are missed.
Virtually all types of businesses can fall victim to fraudulent behavior. For example, there have been scams involving grain silos in Texas inflating their inventory, the sale of mixed oils labeled as olive oil across the globe, and the tens of billions of dollars that Bernie Madoff swindled out of investors and not-for-profits.
To demonstrate how a fraud can occur, let’s examine a sample case in a little more detail. In 2015, a long-term employee of the SCICAP Federal Credit Union in Iowa was convicted of stealing over $2.7 million in cash over a 37-year period. The employee maintained two sets of financial records: one that provided customers with correct information as to how much money they had on deposit within their account, and a second set of books that, through a complex set of transactions, moved money out of customer accounts and into the employee’s account as well as those of members of her family. To ensure that no other employee within the small credit union would have access to the duplicate set of books, the employee never took a vacation over the 37-year period, and she was the only employee with password-protected access to the system where the electronic records were stored.
There were, at least, two obvious violations of solid internal control principles in this case. The first was the failure to require more than one person to have access to the records, which the employee was able to maintain by not taking a vacation. Allowing the employee to not share the password-protected access was a second violation. If more than one employee had access to the system, the felonious employee probably would have been caught much earlier. What other potential failures in the internal control system might have been present? How does this example of fraud exhibit the three components of the fraud triangle?
Unfortunately, this is one of many examples that occur on a daily basis. In almost any city on almost any day, there are articles in local newspapers about a theft from a company by its employees. Although these thefts can involve assets such as inventory, most often, employee theft involves cash that the employee has access to as part of his or her day-to-day job.

